
Unapproachable Telegram has been hacked! — once again the headlines of some media tell us.
But if you look beyond the headings, then the text turns out to be another anecdote from “not a chess player, but a football player, and not 1000 rubles, but 10, and did not win, but lost”.
Let’s look at the statement in the text of an article on one of the news resources and compare it with what another «expert» said.
“A company from St. Petersburg has learned to decrypt the correspondence of users of the Telegram messenger. I told about this in an interview with the educational project «Digital Journalism» … «.
Let’s figure out the process that they describe to us:
- «Special services want to track a specific user» — yes, this is real. Sometimes the secret services want to track someone.
- “We determine through which channel the data is transmitted” — often the choice is small, either a cellular provider or a home Internet provider, there is nothing important here. For a long time, the specialist explains about the search for the connection between the phone and the user, although in real life this is not necessary — usually the surveillance begins with «a person uses this SIM card, let’s monitor the traffic of this SIM card.»
- “Suppose we are the FSB and come to the operator” — technically, this is not entirely legal without a court order, but we have already had cases when mobile operators accidentally forgot to ask about the legality of requirements and quite accidentally allowed the special services to do what they wanted.
- “[And the FSB asks] to drive all user traffic through the THRUSTER and decryption” — we in the editorial office did not understand why a certain Thresher was introduced into this, until now, real story. The expert further explains that using this special tool, you can sort traffic, separately receiving encrypted Telegram traffic. There is only one caveat — telecom operators and without any HAMMERS are able to identify and sort traffic by destination. This is how any tariffs with free traffic “to messengers or music services” and the like work.
Up to this point, we see a completely adequate story — the special services can get access to the user’s traffic, which the operators have undertaken to store for some time according to the Yarovaya packet. And now the time has come for extraordinary stories:
- “[And this received encrypted Telegram traffic] we can easily decrypt it. Basically, I saw a development for decrypting non-secret Telegram chats. She is in St. Petersburg. «
If the points before that were very vital, with the exception of the word HAMMER, then the last point raises doubts. In the third minute of this interview, the presenter tries to get details about what is seen as a result of the decryption, but the conversation goes into the jungle and no more specific information appears.
As a result, in an interview with an educational project, the guest stated that he saw someone in St. Petersburg develop a program to decrypt non-secret chats.
It’s time to talk, how exactly are non-secret chats encrypted? Why are they worse than «secret chats»? Why do celebrities complain that group cloud chats don’t use endpoint encryption?
To simplify a bit, your non-secret chat message is encrypted using SHA-256. And if not to simplify, here’s a picture to help you and a link to the documentation of the MTProto protocol.
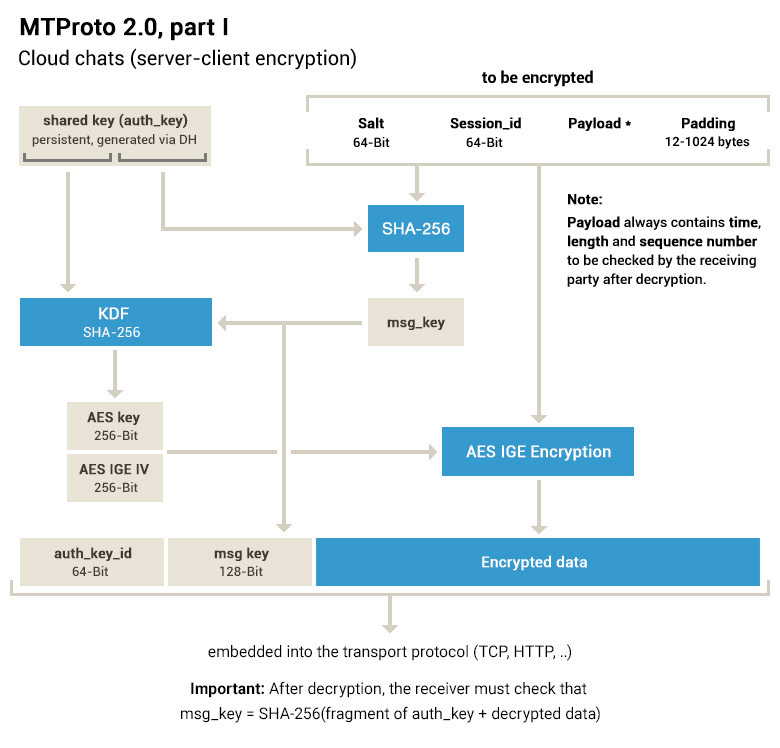
The encrypted message leaves your phone, the operator sees this encrypted message and transmits it to the Telegram servers, where it is decrypted. Some see this as a problem for non-secret chats — a theoretical Evil Durov with access to servers can read your correspondence (with some difficulty, since the decryption key is stored in parts on other servers in several countries with different jurisdictions, but theoretically it can).
But at the operator level, it’s still encrypted with SHA-256.
And some people, according to the expert, know how to crack SHA-256. To read a person’s messages in a messenger. Where else is this apparently simple hash function used? It’s no big deal, just by all government agencies, just in any protocol, for example, SSL, TLS, SSH. Any cryptocurrency, for example Bitcoin, uses SHA-256 to verify transactions. If you know how to crack SHA-256, then there is no point in working for the FSB — you can buy yourself an FSB by drawing any amount of money.
But if the expert said that he personally saw the development of decrypting non-secret chats, then there is nothing to be done, you have to believe.🤷♂️
The author of this text transfers all his money to buckwheat and stew and goes to live in the forest, away from any modern encryption protocols.
PS When the secret services want to receive your correspondence, they will come to you personally, take your equipment, and the responsible persons will turn away at the right time so as not to assess the legality of the methods of obtaining passwords and fingerprints to unlock the device. Although no, such arbitrariness is impossible in your country?